Welcome to another enlightening guide! Over the past months, I’ve delved deep into various CTF writeups, always emphasizing the importance of a streamlined cybersecurity lab setup. While many of you have successfully navigated through the Kali Linux installation using our detailed guide, I’ve noticed a recurring query: How do we kickstart our journey with TryHackMe? It’s a valid question and one that deserves its spotlight. So, here we are! This article is dedicated to guiding you meticulously through the TryHackMe setup process, ensuring you’re well-equipped to dive into the world of cybersecurity challenges.
Let’s embark on this journey together, ensuring every step is clear and actionable.
What Is TryHackMe?

Let me introduce you to TryHackMe, a platform tailored just for you. At its core, TryHackMe is a dynamic, browser-based training platform designed for every budding hacker out there. It’s a platform designed both for novices and seasoned pros.
TryHackMe offers gamified lessons that are not just educational but downright addictive. Imagine earning points while you learn, keeping you motivated throughout your journey. And it’s not just about theory. The platform emphasizes hands-on learning, allowing you to practice in real-world environments, and tackle challenges that hone your skills.
But what truly sets TryHackMe apart is its community. It’s vast, vibrant, and filled with individuals just like you. Here, you can connect, share knowledge, ask questions, and embark on a shared journey of discovery.
In essence, whether you’re starting from scratch or aiming to stay updated with evolving threats, TryHackMe is your go-to platform. It’s not just about learning; it’s about experiencing, practising, and growing in the realm of cybersecurity.
What Is A VPN?
A VPN, short for Virtual Private Network, is like a protective bubble in the vast ocean of the internet. Imagine you’re sending a secret letter to a friend. Instead of sending it openly, where anyone can read it, you put it inside a secure envelope. This envelope ensures that only your friend can open and read the letter. Similarly, a VPN acts as this secure envelope for your online data, making sure it travels safely without prying eyes intercepting it.
When you’re online, especially on public networks like cafes or airports, your data can be easily accessed or stolen. A VPN encrypts this data, turning it into a complex code. Even if someone intercepts it, they won’t understand it. It’s like turning your open letter into a secret language that only you and your friend understand.
Now, let’s relate this to the TryHackMe setup. To access the challenges and machines on TryHackMe, you need to connect through their VPN. This ensures you have a direct, shielded connection to their platform. It’s like having a private training room in a vast library. Inside this room, you can practice hacking safely, without the fear of causing real-world harm or being watched. The VPN ensures your activities remain within this room, separate from the real internet. This way, you can focus on learning and experimenting, confident in the knowledge that you’re in a secure and controlled space.
Registration
Finally, after a long but necessary introduction, we are ready to setup our TryHackMe account!
Kick things off by launching your browser on your Kali Linux machine. Head straight to https://tryhackme.com.

Spot the “Join Now” button on the homepage. Click it.
You’ll land on the sign-up page. Here, you have two options: fill out the form or simply use your Google account to sign in.

If you opt for Google, select your account and answer a few questions. This helps tailor your TryHackMe experience.
You might see a prompt to enter your email. It’s optional. Feel free to skip by hitting “Skip Now”.

Next, TryHackMe presents you with learning paths. Each has its unique focus:
- Red Teaming: Dive deep into advanced offensive tactics. This path equips you with skills to simulate cyber-attacks, testing an organization’s defences.
- Soc Level 1: Begin your journey in cybersecurity operations. Learn to monitor, detect, and respond to digital threats in real time.
- JR Penetration tester: Lay the foundation for ethical hacking. Understand vulnerabilities, exploit weaknesses, and safeguard systems.
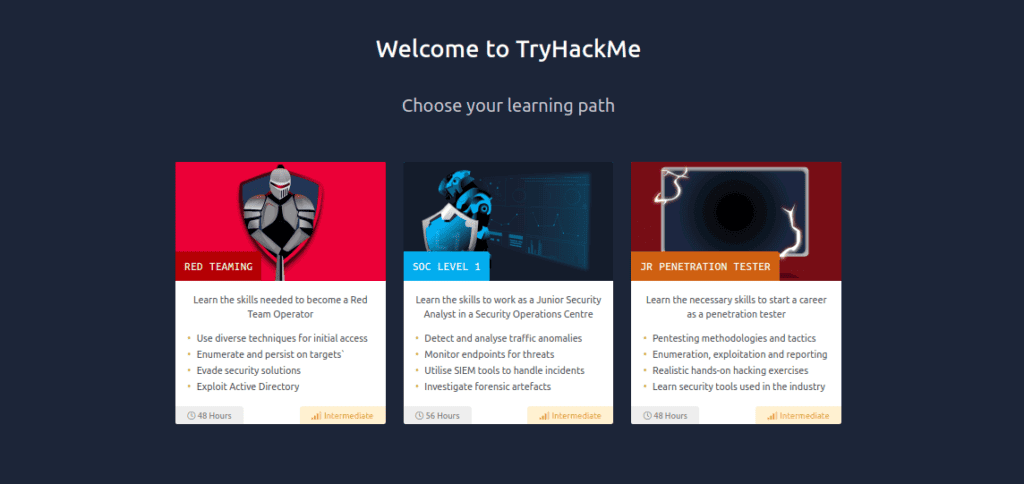
Your cybersecurity journey is about to begin. Pick the path that aligns with your goals.
For the sake of this guide, I’ll select “Red Teaming”. Here’s what the next screen looks like:
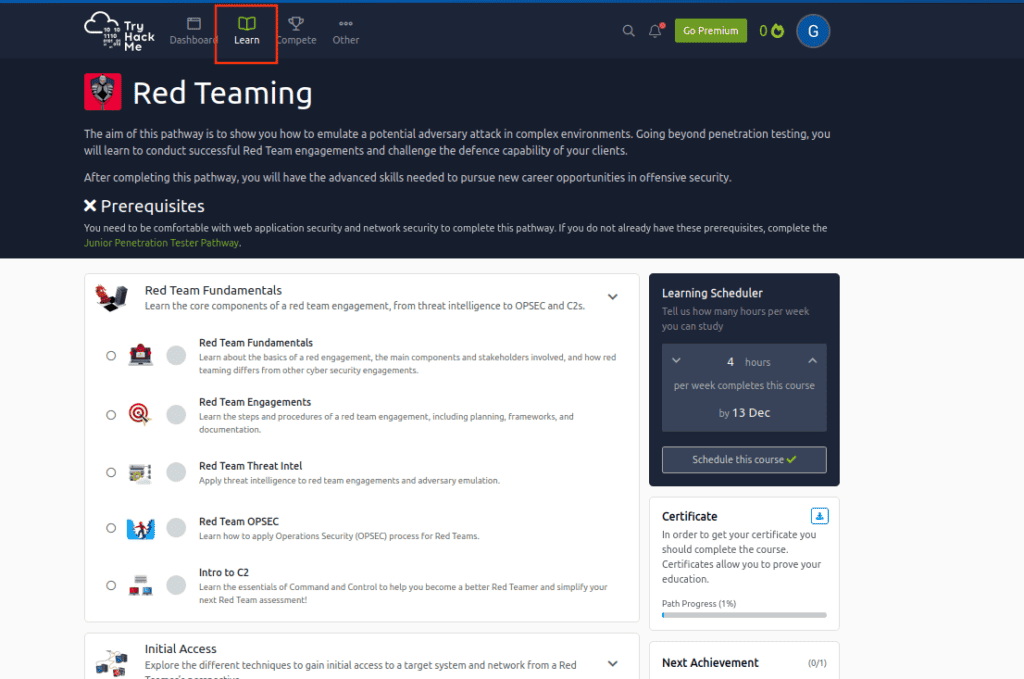
Navigate to the “Learn” tab, then click “Search”. Enter “DVWA” in the search bar.
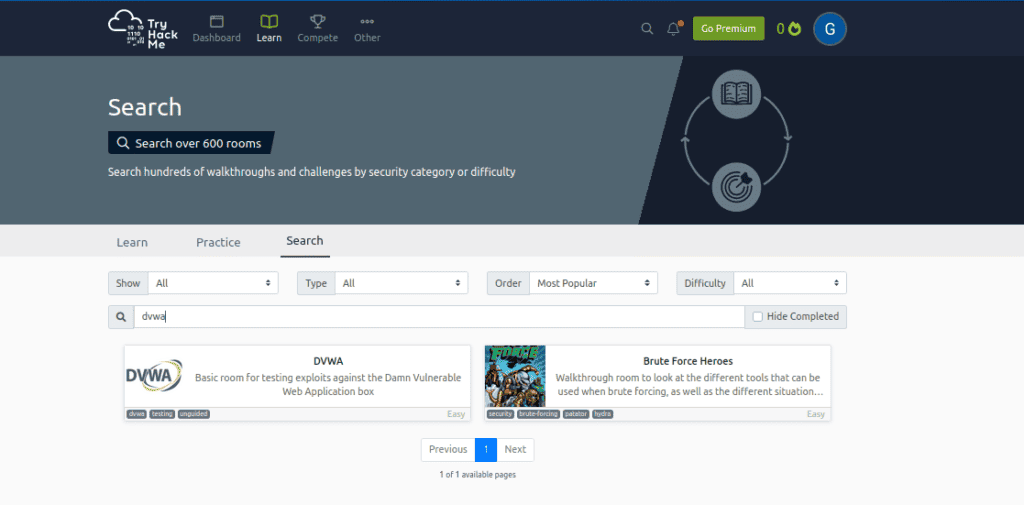
All set! Click on the machine you want, and gear up to launch it.

Setting Up Your TryHackMe Machine: A Step-by-Step Guide
Embarking on your TryHackMe journey? Let’s get you connected seamlessly.
Join the Room: Before diving in, heed the alert’s advice. Click “Join this room”.
Power Up: Hit “Start Machine”. Note: You don’t need Kali for this step.

Connection Choices: Post activation, TryHackMe offers two connection options: VPN or the Attack Box.
- Attack Box: A browser-based Kali machine. It’s user-friendly but might lag. Plus, it’s not complimentary.
- VPN: Our choice for this guide. It’s efficient and free. Click “See Instructions”, leading you to the download page for the VPN configuration file.
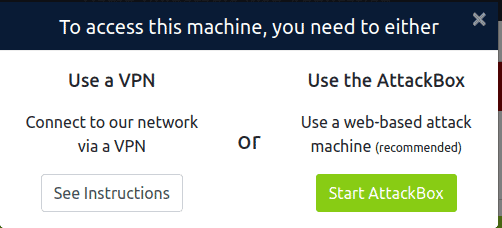
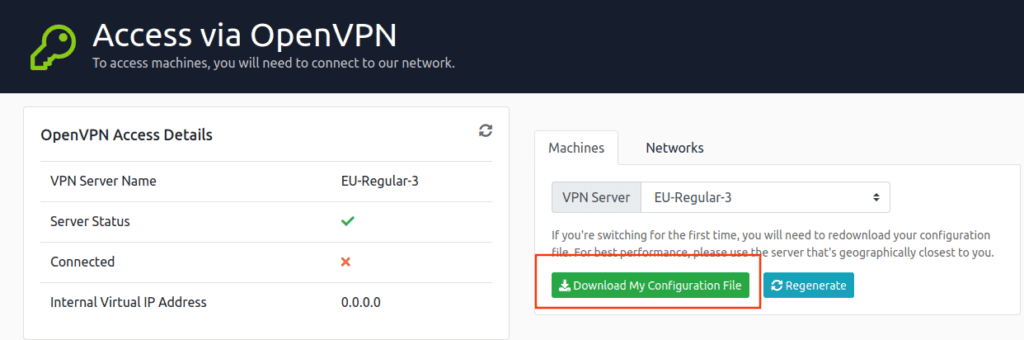
VPN Configuration:
- Download the highlighted VPN configuration file.
- Navigate to the file’s location (typically ‘Downloads’).
- Open a terminal here.
- Run the command:
sudo openvpn porpoisepropheti.ovpn(Replace ‘porpoisepropheti.ovpn’ with your file’s name). - Input your password, hit enter, and watch the connection magic happen.
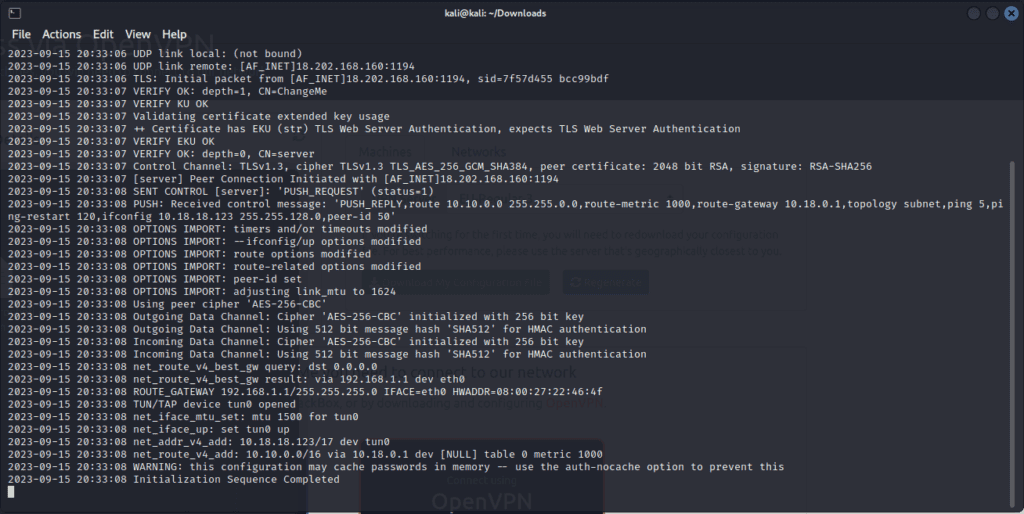
Test the Connection:
- Return to TryHackMe.
- On the machine’s start page, locate the IP Address.

Copy this IP, paste it into your browser’s address bar, and press enter.

If your screen mirrors the image above, kudos! Your TryHackMe setup has been successful, and you’re all set to dive into the world of challenges.
Concluding Your TryHackMe Setup Adventure
Navigating the TryHackMe setup might have seemed intricate at first glance. But, step by step, with a touch of guidance, you’ve now laid the foundation for numerous cybersecurity challenges that await. Tools like TryHackMe aren’t just platforms; they’re gateways to mastering the art of cybersecurity, bridging theoretical knowledge with hands-on experience. With your setup in place, you’re all set to delve deeper and refine your hacking prowess. As you embark on this journey, don’t forget to actively follow my blog at Stackzero for more insights, tutorials, and cybersecurity wisdom. Dive in and happy hacking!







