Diving into the realm of Capture The Flag (CTF) challenges? PicoCTF stands out as a prime starting point. While I’ve covered numerous topics on Stackzero.net, today’s focus is a step-by-step guide to ease your PicoCTF registration process. After mastering the basics of cybersecurity, it’s time to test those skills. And what better platform than PicoCTF? By the end of this guide, you’ll be set up and ready to tackle the challenges that await.
What is a CTF?
Capture The Flag, or CTF, isn’t just a childhood game. In the cybersecurity world, it’s a challenge. A test. Participants dive deep into security puzzles, aiming to find flags – snippets of data that prove a task’s completion. Think of it as a digital treasure hunt. Each flag captured scores of points. The more complex the challenge, the higher the points. CTFs come in two flavours: Jeopardy-style, where challenges are categorized, and Attack-Defense, where teams defend their servers while attacking others. It’s a hands-on way to learn, practice, and showcase cybersecurity skills.
What is PicoCTF?
Enter PicoCTF. Designed by cybersecurity experts at Carnegie Mellon University, it’s a platform tailored for all – from beginners to seasoned pros. PicoCTF offers a unique learning curve. Challenges start easy, ideal for beginners, and gradually ramp up in complexity. But it’s not just about solving puzzles. PicoCTF embeds a storyline, making the experience immersive. As you navigate challenges, you also unravel a narrative, making the learning process engaging. It’s more than just a platform; it’s a community. A place to learn, grow, and connect with others on the same cybersecurity journey. Whether you’re a student, a professional, or just a curious soul, PicoCTF offers a world of challenges waiting to be conquered.
Starting Your PicoCTF Journey: Registration
Kick-off by heading to https://picoctf.org. Spot the “Log in” button on the top right? Click it.
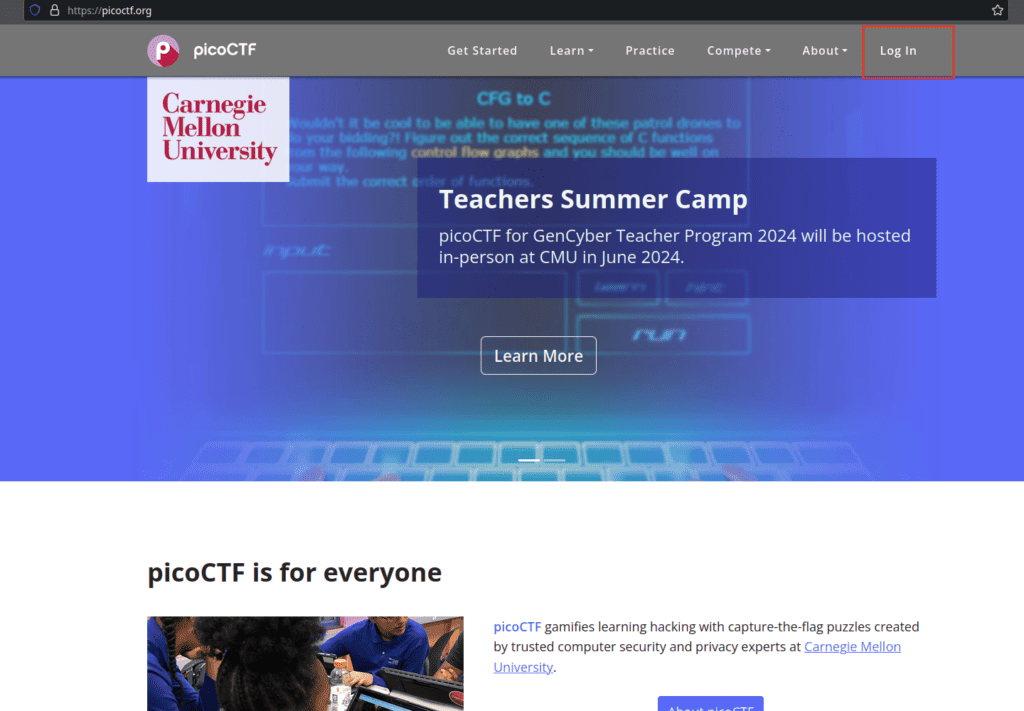
Next, you’ll see a “Sign Up” link. Please give it a click.

Time to pick a unique username and fill out the necessary details.

Filled everything? Great. Hit the “Sign Up” button. What you’ll see next should look like this:
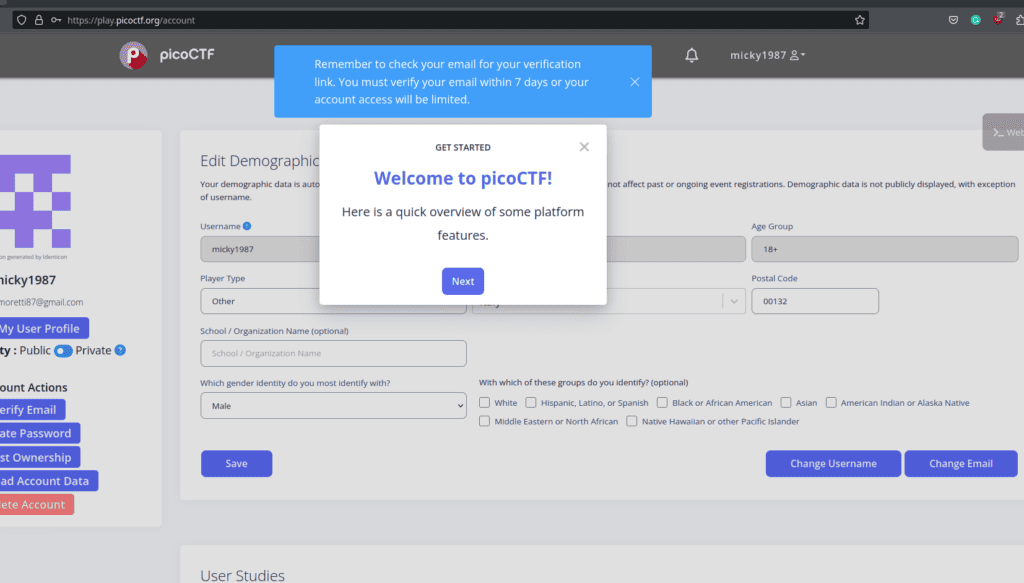
But wait, there’s a catch. You’ve got 7 days to confirm your email. So, dash to your inbox. Look for a confirmation link from PicoCTF. Found it? Click on it.
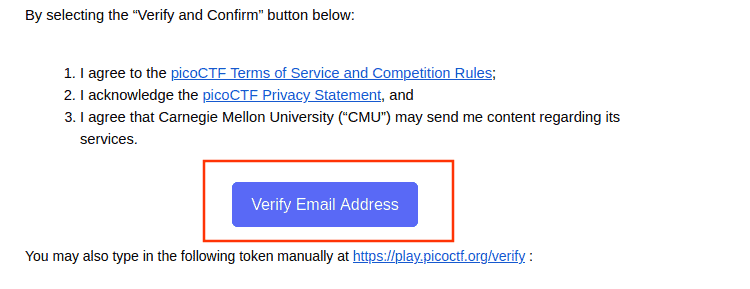
And just like that, you’re all set.
Dive into the world of CTF challenges on PicoCTF and hone your skills!
Diving into PicoCTF Challenges
Ready to explore? Click “Practice” on the main menu.
Now, take a glance at the left sidebar. It neatly categorizes all the CTF challenges.
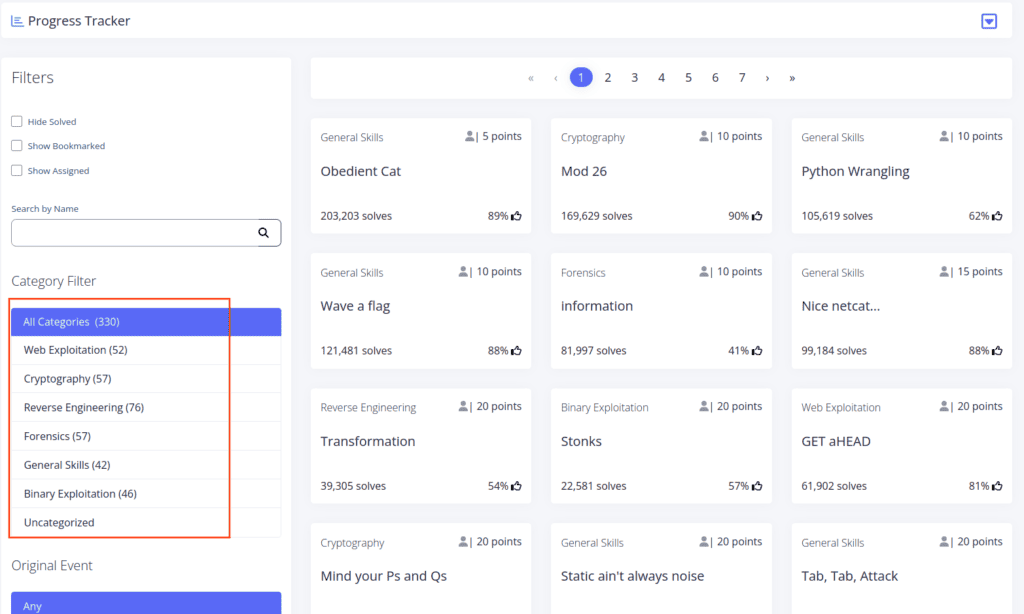
Here’s a breakdown of the categories:
- Web Exploitation: Dive into the intricacies of web vulnerabilities and security.
- Cryptography: Decode secrets and understand encryption techniques.
- Reverse Engineering: Dissect software to understand its core functions.
- Forensics: Unearth hidden data and investigate digital clues.
- General Skills: A mix of essential skills every hacker should master.
- Binary Exploitation: Delve deep into binary files and exploit their vulnerabilities.
Choose a category that piques your interest and start your PicoCTF journey!
If you don’t know where to start, here is a good starting point where you can learn a bit more about picoCTF and hone your general skills!
Wrapping Up Our PicoCTF Registration Guide
Navigating the world of CTFs can be daunting, but with this PicoCTF Registration Guide, you’re now well-equipped to embark on your cybersecurity journey. Remember, every challenge you face is a step closer to mastering the art of hacking. If you found this guide helpful, consider following our blog and our social media channels. We’re constantly updating with fresh content, insights, and more guides to help you stay ahead in the cybersecurity realm.
Stay curious, keep learning, and until our next article, happy hacking!







