In this article, we will crack Cesar’s cipher on a PicoCTF challenge using our beloved Python.
We have already talked about the Caesar cipher, both in theory and in practice, if you missed the previous article here the links:
- Substitution ciphers? An overview of the basics: A theoretical part on substitution ciphers.
- Secret Codes Unlocked: How to Implement Substitution Ciphers: A step-by-step tutorial on implementation of some of the discussed ciphers.
Let’s take a quick trip back in time to explore the famous Caesar’s cipher, a classic cryptography system from ancient times. Named after Julius Caesar himself, this nifty technique was his go-to method for sending secret messages to his top generals.
Implementing this algorithm just requires shifting each letter in a message just a few spots down the alphabet, and voilà, you’ve got a secret code.
The number of spots is the key, for example, with a key of 3, A transforms into D, B turns into E, and so on. The recipient has to simply reverse the shift, and the original message reveals itself.
Back in the day, Caesar’s cipher was a real game-changer. With only a handful of literate folks around, and even fewer multilingual, it kept secrets safe. Fast forward to today, though, and computers can crack this code in the blink of an eye (even if a patient person can brute-force it manually in a short time).
Despite its simplicity, it’s still a favourite for cryptography newbies and coding enthusiasts alike.
The Challenge
Dive into the world of CTF challenges with our latest task, where you’ll be cracking a code to reveal the hidden flag nestled between “picoCTF{” and “}“. This thrilling challenge will have you flexing your Python skills as you brute force your way through every possible shift in a lowercase alphabet.
The real excitement here lies in identifying the successful attack. But don’t worry, even though it might seem like finding a needle in a haystack, there are telltale signs that’ll guide you to the correct key. You’ll be one step closer to victory with each output meticulously inspected.
So, put on your cryptography hat, and join us in this exhilarating CTF adventure. Unleash the power of Python and uncover the secrets behind every shift, leaving no stone unturned in your quest for the elusive flag. This challenge will not only test your skills but also inspire you to push the boundaries of your knowledge in the captivating realm of cybersecurity.
Where Can I Crack Cesar’s Cipher In PicoCTF?
The challenge I’m going to illustrate belongs to a very beginner-friendly website that can take us into the amazing world of CTF: PicoCTF.
What Is A CTF?
Before talking about PicoCTF and solving the challenge I want to briefly describe what is a CTF.
A CTF is a type of competition where teams or individuals compete to find hidden “flags” in computer systems or networks. These flags are usually text strings or codes that represent some sort of secret that needs to be protected.
They are often used in cybersecurity training and education, providing a safe and controlled environment for people to learn and practice hacking techniques and strategies.
What Is A PicoCTF?
PicoCTF is an online Capture the Flag competition that’s designed for beginners who want to learn more about cybersecurity. It’s a free and safe way to practice hacking skills and learn more about cybersecurity concepts.
It has also a well-designed practice platform with increasingly difficult challenges that are grouped by topic. So It is gold for those who want to approach cybersecurity, I’m sure you will like it.
Here is a complete tutorial if you are starting from zero and you have no idea of what is PicoCTF and how to register!
The Challenge
- The first step to try to solve our puzzle is to register to picoCTF from this address.
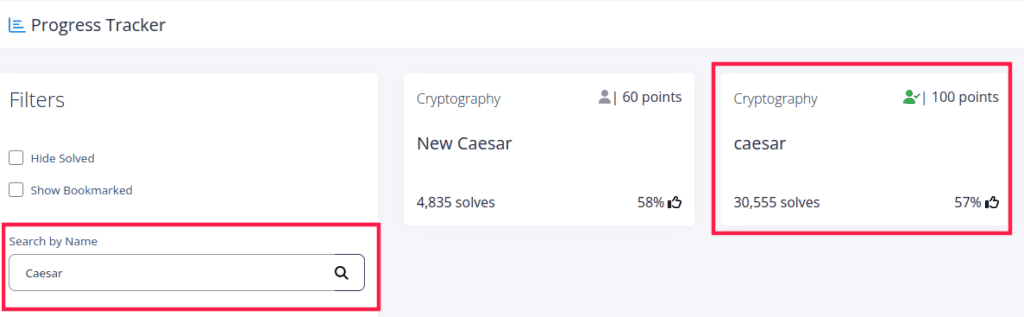
- Once you are inside, click on “Practice” in the top menu and you should see a search button in the left sidebar.
- Now you can type “caesar” and search!
The challenge asks you to decrypt the message.

The message inside the file is the following one.
picoCTF{dspttjohuifsvcjdpoabrkttds}That’s our flag, so now we are ready to crack Cesar’s cipher! Let’s go to the next section!
The Solution
Those familiar with picoCTF probably already know that the flag format is picoCTF{<flag>}.
Therefore, we can guess that the part to be deciphered is only the part in curly brackets.
The strategy we will use here is to try all possible combinations, print the results on the screen, and try to recognize a plaintext that makes sense among all of them.
But let’s see the script in practice before commenting on it step by step (I assume to have the file in the same folder as the script).
import string
alphabet = string.ascii_lowercase
def shift_cipher(cipher_text, key, alphabet):
return "".join([alphabet[(alphabet.index(c)+key)%len(alphabet)]if c in alphabet else c for c in cipher_text])
with open("ciphertext") as f:
cipher_text = f.read()
for i in range(len(alphabet)):
plain_text = shift_cipher(cipher_text, i, alphabet)
print(f"Key: {i}: {plain_text[8:-1]}")
Here’s a simplified explanation of the code:
- Import the
stringmodule to get access to the alphabet. - Define the
alphabetvariable as the lowercase English alphabet. - Define the
shift_cipherfunction that takes three arguments:cipher_text,key, andalphabet.
The function returns the decrypted text by shifting each letter in thecipher_textby thekeyvalue in thealphabet. - Open the file “ciphertext” and read its content into the variable
cipher_text. - Loop through all possible shift values (0 to 25) and apply the
shift_cipherfunction to thecipher_textwith each shift value. - Print the decrypted text for each shift value, along with the shift value itself (the key).
Now you can observe all the results and decide what is the right one.
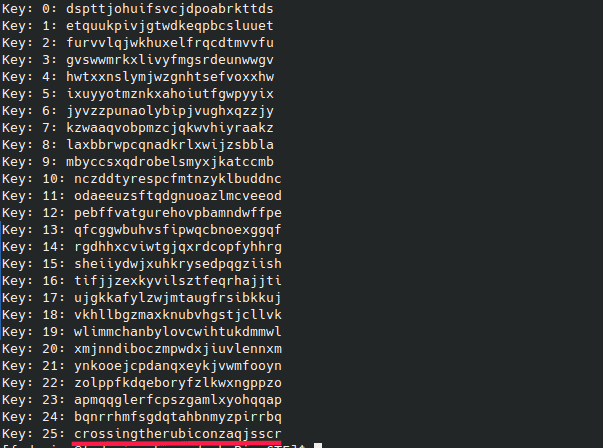
Our flag that would prove we cracked Cesar’s cipher is:picoCTF{crossingtherubiconzaqjsscr}
So let’s try that input and see if we found the key!
Yep! It worked!

Conclusion
In conclusion, you learned how to crack Cesar’s cipher with Python in a picoCTF challenge and I guess you found it a fun and exciting way to learn about cryptography!
By understanding the basics of the Cesar cipher and using a simple brute-force approach, you’ll be able to tackle and solve this challenge with confidence.
I hope this article has inspired you to dive deeper into the world of cryptography and Python programming. Don’t forget to follow our blog for more exciting content like this, and stay updated on our latest adventures in cybersecurity and programming! You can also find us on Medium, GitHub, Instagram, and Twitter to stay connected and be the first to know about new articles, challenges, and tips.
Together, let’s continue exploring and conquering the fascinating world of cryptography!
Happy hacking, and see you in the next challenge!







