Navigating the internet can be full of surprises. We find amazing discoveries and clever scams. One trick involves a Python tool called mitmproxy. Some online “financial gurus” use it. They want to make it look like they have lots of money in their bank account.
We’re not just here to point out this trick. We want to study it. We want to understand how this online scam works. It’s important to be careful on the internet. We need to know how it works to stay safe.
The Python script we’re looking at is sneaky. It makes a fake bank balance look real. Even when you refresh the page, the fake balance stays the same. But remember, this is just one trick.
We’ll take our time to understand this. We’ll break it down into simple steps. Everyone should be able to understand how this scam works. The more we know, the safer we can be on the internet.
Let’s start our journey. Let’s introduce mitmproxy Python library.
Setting the Stage: Your First Steps into the Cyber Lab with Mitmproxy for Python
Ready to delve into this simple tutorial? Setting up a cyber lab to test our proxy is a piece of cake.
We kick off with Kali Linux, heaven for cybersecurity and pentesting lovers. So, start your Kali Linux machine and let’s plunge in.
Next, we’ll scoot over to the directory where we’ll save our files. This is where the magic comes to life. Fire up the terminal and let’s get to work:
git clone https://github.com/StackZeroSec/fake_bank_account_article.gitThat simple command clones the repository into your chosen directory. Now, you’re free to tinker and test. Then, trot over to the “html” folder:
cd htmlIt’s time to launch the server with Python:
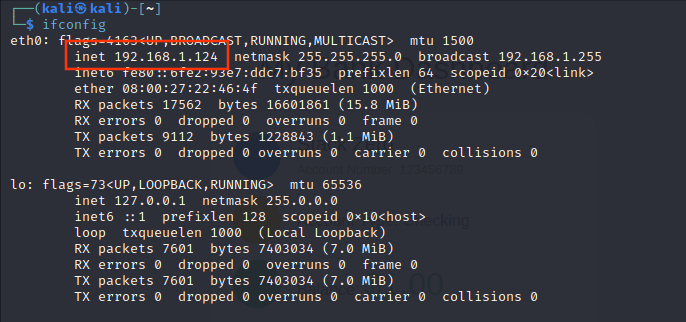
python -m http.serverBefore looking at our results, we want to know our IP address, so type this command in your terminal:
ifconfigIn my case, this is the result (I highlighted the IP address)
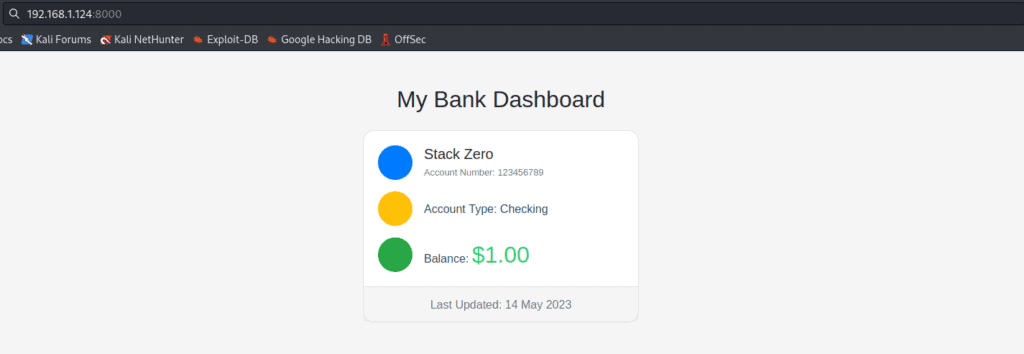
To confirm everything is humming along, open Firefox. Type http://192.168.1.124:8000 in the address bar and press enter.
And there it is!
We’re gaining momentum, aren’t we? But we’re not done.
Now, we set our sights on the target – the account balance. Right-click on it and hit “inspect”.

Please take note of the class of our target. It’s “balance”. But hold on! Before we sprint ahead, let’s pause and set up the proxy in Firefox.
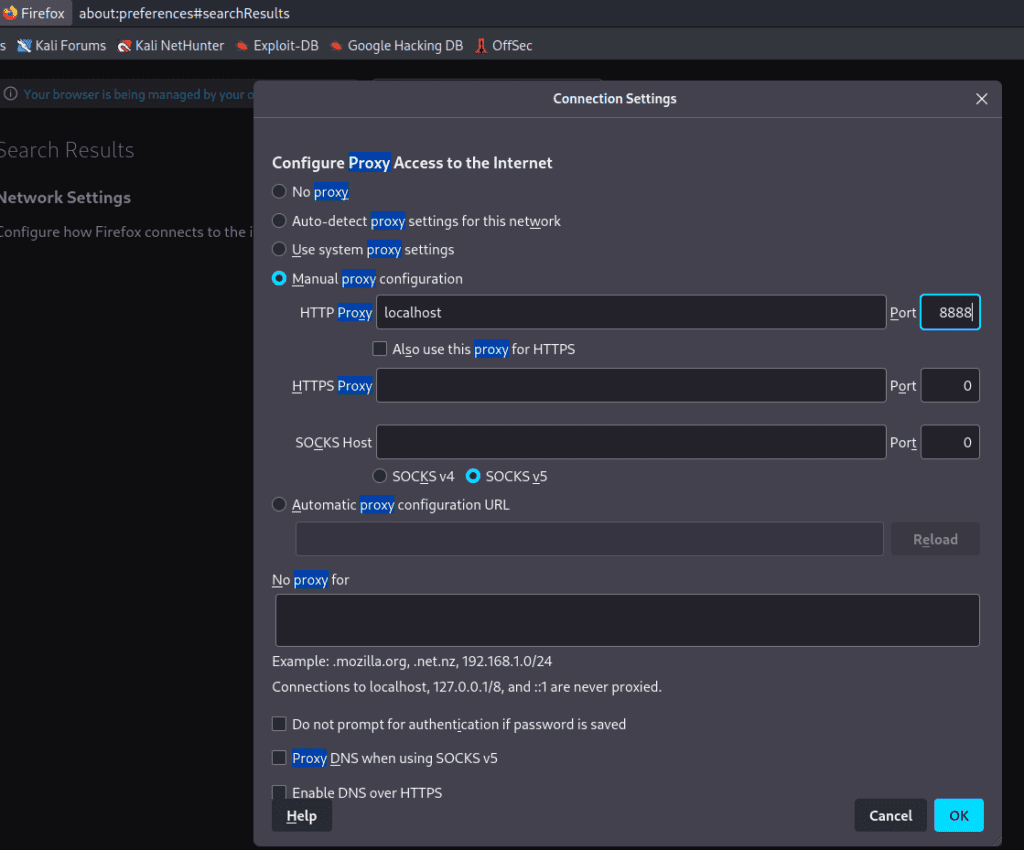
- Head over to Firefox’s settings.
- Hunt for “Proxy”.
- Set the manual proxy configuration to “localhost” and the port to “8888”.
- Don’t forget to tick the box for “Use this proxy server for all protocols”.
We’ve gathered all the info needed for our trick. But patience, we’ll unfold the next steps in the upcoming paragraphs.
How to install an SSL certificate for Mitmproxy
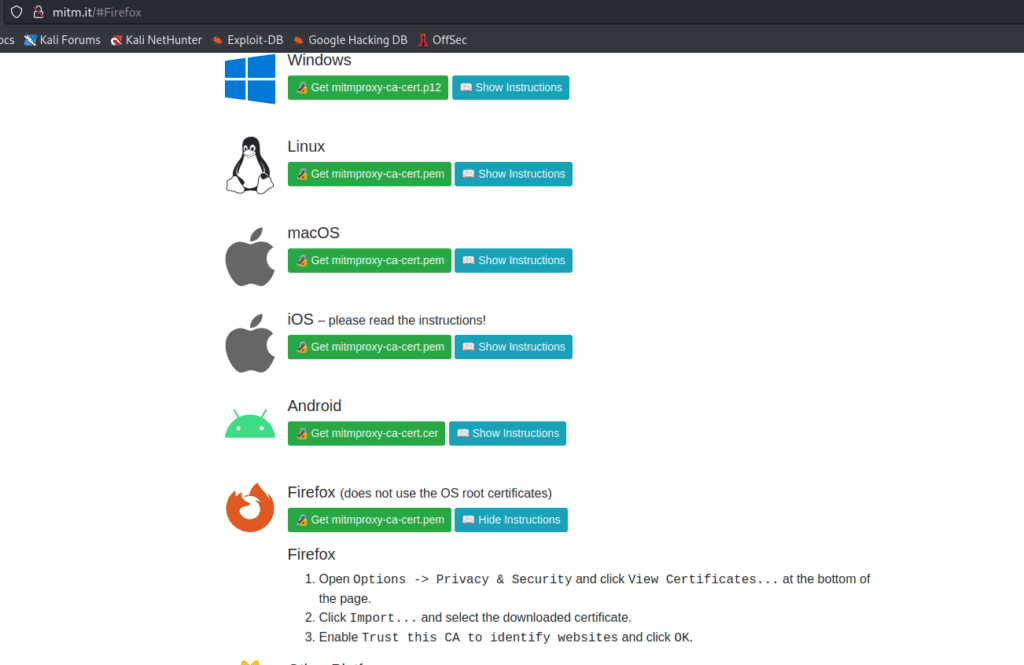
We want to do things properly as they do. This includes creating an SSL certificate. To make this easier, I’ve put one in my repository. But you can also get it yourself. Just go to “http://mitm.it/” on your browser once you activated the proxy.
The instructions on how to install it are on the website. You can see them in the screenshot.
But here is an alternative and painless way:
- Visit the website.
- Download the Mozilla certificate.
- Move it into the same folder as the script.
- When you run the script, include the certificate. Use this command: ‘–certs *=mitmproxy-ca-cert.pem’.
It’s that simple. Now you’re ready to start.
Behind the Scenes with Proxy Servers
Let’s take a peek at a vital yet unnoticed part of the networking world – the proxy server. This middleman skillfully handles traffic between your computer and the server hosting the website you’re browsing. But what if this quiet mediator starts stirring the pot?
A self-proclaimed guru could craftily use a Python script to set up a proxy server. This server doesn’t just pass on traffic but alters the content of web pages as they flow through it.
Mitmproxy Python, a versatile, interactive proxy, enables users to intercept, scrutinize, modify, replay, and record HTTP and HTTPS traffic.
Mitmproxy with Python practical example
Here’s a snapshot of what the script could look like:
import mitmproxy.http
from mitmproxy.tools.main import mitmdump
def response(flow: mitmproxy.http.HTTPFlow):
if '<span class="balance">$1.00</span>' in flow.response.text:
flow.response.text = flow.response.text.replace('<span class="balance">$1.00</span>', '<span class="balance">$10,000,000.00</span>')
print('Replacement made!')
if __name__ == "__main__":
mitmdump(['-s', __file__, '-p', '8888', '--certs', '*=mitmproxy-ca-cert.pem'])
When an HTTP response navigates through the proxy, the response function gets into action. It scans for the text ‘<span class=”balance”>’ in the HTTP response. If this text is present, the function takes action, switching the balance to a whopping ‘10,000,000’. Here, Python’s built-in replace function comes into play. We know exactly what we’re going to replace, so we can use this “weak” approach.
However, in real life would be better to rely on regular expressions.
Next on the agenda is calling mitmdump with the -s option. This propels Mitmproxy into script mode. We pass along the name of the current script file (__file__) as the script to be executed.
So, the Python script essentially “activates itself” under Mitmproxy’s wing.
Take note that this script requires Mitmproxy to be installed and correctly configured on your system. You can do this with a quick command:
pip install mitmproxyNow, about the “–certs” part. This is a command-line option that specifies the location and name of the SSL certificate file used by the proxy. In our case, ‘=mitmproxy-ca-cert.pem’ means that we’re using a custom SSL certificate file named ‘mitmproxy-ca-cert.pem’ for all hosts (‘‘ is a wildcard that stands for all hosts).
This certificate file is necessary for the proxy to decrypt and inspect HTTPS traffic. So, the “–certs” option tells Mitmproxy to use this particular certificate for all SSL communications passing through it.
Just for simplicity, as I previously said, I attached the required file to the GitHub repository in the “proxy” folder.
Unmasking the Digital Illusion
And now we can see that the final result of our Python script with mitmproxy is exactly what we expected!
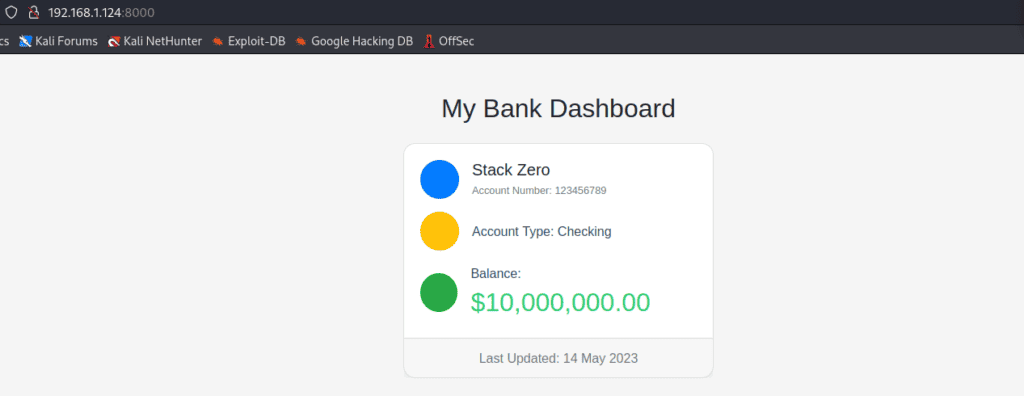
This handy tool can be used by online “financial gurus” to exaggerate their wealth and make them seem more successful than they indeed are.
What we’re diving into isn’t merely a trick. It’s an in-depth study of how this digital deception operates. This is a wake-up call for everyone to exercise caution, for the online world is a complex labyrinth where appearances can be deceiving.
This unique Python script catches our attention. It’s engineered to fake a bank balance convincingly. Refreshing the page doesn’t bring the truth to light but reinforces the illusion, making the inflated balance seem real.
Obviously, this is just a rare usage of the proxy server, but we proved how can be used creatively to trick ingenuous viewers.
Closing the Curtain: Demystifying the Web with StackZero
As we draw the curtains on our exploration of Python-scripted proxy servers, we hope you’ve found this journey as intriguing as we did. This vast digital landscape is full of wonder and mystery, with every corner holding a surprise waiting to be discovered and understood. As we navigate this vast expanse, it’s essential to be armed with the right knowledge and skills, which is where StackZero comes in.
At StackZero.net, our mission is to demystify the digital realm, revealing its inner workings one piece at a time. We are passionate about technology, keen on unravelling the intricacies of the web, and excited to share our findings with curious minds like yours. This adventure is far from over – it’s just the beginning of our exploration into the depths of the internet.
Follow our blog for more fascinating insights into the technological tricks that shape our online experiences. We’ll be diving into a variety of topics, exploring the complexities of coding, network infrastructure, security practices, and much more. As we learn together, we hope to inspire you and stir your curiosity, make you question, explore, and most importantly, understand.
Don’t forget to join us on our social media platforms as well. Be a part of our community, interact with like-minded technology enthusiasts, and let’s unravel the mysteries of the digital world together.
Remember, in the internet world, things are not always as they seem. Keep your eyes open, keep questioning, keep learning, and always stay curious. See you on the next adventure!







